Cisco OSPF Basic Configuration In this Cisco CCNA tutorial, you’ll learn how to do a basic configuration of OSPF on our Cisco routers. Scroll down for the video and also text…
Cisco Slash Notation

In this Cisco CCNA tutorial, you’ll learn how to write and convert the dotted decimal subnet mask into slash (/) notation, Cisco Slash Notation.
Subnet mask in “Slash Notation” is a simplified way of representing the subnet mask in IP (Internet Protocol) networking. In traditional subnet mask notation, the subnet mask is expressed as four numbers separated by dots, such as “255.255.255.0.” However, in Slash Notation, the subnet mask is represented by a single number that follows the IP address and is separated by a forward slash (“/”).
The Cisco Slash Notation format represents the number of consecutive 1 bits in the binary representation of the subnet mask. These 1 bits determine the network portion of the IP address, while the remaining 0 bits represent the host portion. Here’s how it works:
Let’s take an example of a subnet mask in traditional notation: 255.255.255.0
- Convert the subnet mask to binary: 255 in binary is 11111111 (8 ones in binary). So, the subnet mask in binary is 11111111.11111111.11111111.00000000
- Count the number of consecutive 1 bits in the binary representation. In this case, there are 24 consecutive 1 bits.
- Represent the subnet mask in Slash Notation: /24
So, the subnet mask in Slash Notation for the subnet mask 255.255.255.0 is /24.
Here are a few more examples for better understanding:
- Subnet mask: 255.255.255.240 Binary: 11111111.11111111.11111111.11110000 Slash Notation: /28
- Subnet mask: 255.255.0.0 Binary: 11111111.11111111.00000000.00000000 Slash Notation: /16
Using Cisco Slash Notation can make it easier to represent and compare subnet masks, especially when dealing with different-sized subnets in IP networking. It simplifies the subnetting process and helps network administrators quickly identify the size of a subnet.
Now, Let’s understand it by giving some closure look:
Subnet Mask in Slash Notation
In the example below, the subnet mask 255.255.255.0 is in decimal notation. We can write the subnet mask in binary, and you can see a line between the network and host portions. It’s always contiguous 1’s and then followed by a block of contiguous 0’s. Because it’s contiguous, we can count how many 1’s that we have in a row.
Here, we have got 24 1’s in a row. Each block is an octet (8), so that’s 8, 16, 24. Therefore the dotted decimal notation 255.255.255.0 can be written as /24 in slash notation. Those two things both mean the same thing.
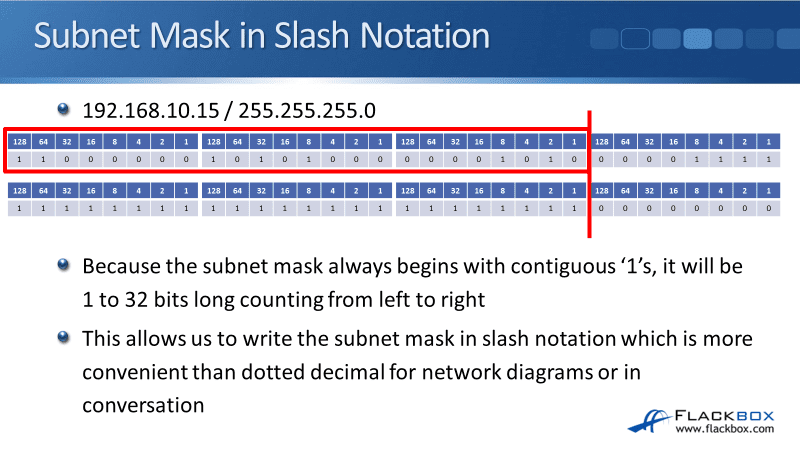
If we had 255.255.0.0 as a subnet mask, we could write that as /16, and so on. Whenever you configure a Cisco router or switch on IOS, the IP address and the subnet mask configuration are written out in the full dotted decimal notation. But whenever we’re having a conversation with somebody, or if we are creating a network diagram, more commonly, we will use slash notation.
It’s not much fun to be saying 255.255.255.0 all the time. It’s much easier to say /24. Also, /24 takes up much less space on your network diagrams, so you can have your diagrams looking a lot neater and tidier. There’s the network portion for a /24 highlighted.
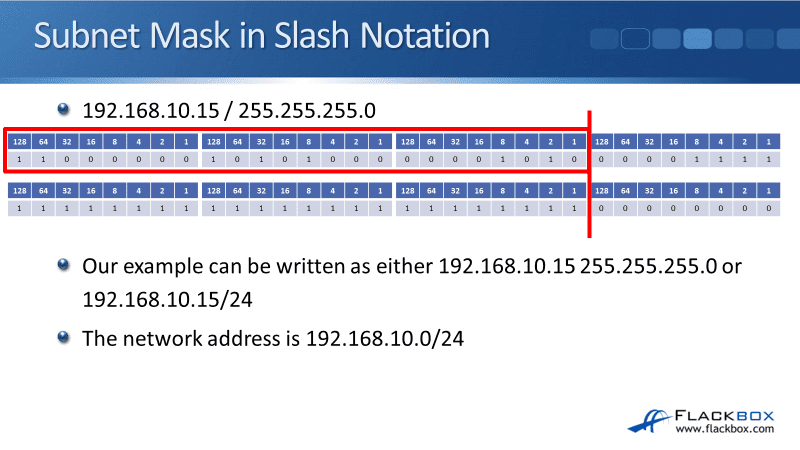
Subnet Mask in Slash Notation Example 2
Let’s look at another example. We have IP address 10.10.10.15 /255.0.0.0, and hopefully, you can just by looking at this, you’re going to see that that’s going to be a /8. The more you get used to working with IP addresses and subnets, you’ll very quickly be able to see where the lines are by just looking at the actual address and mask.
In the example below, the IP address can be written as 10.10.10.15 255.0.0.0 or 10.10.10.15/8. The network address is 10.0.0.0/8, not 10.10.10.0 /8.
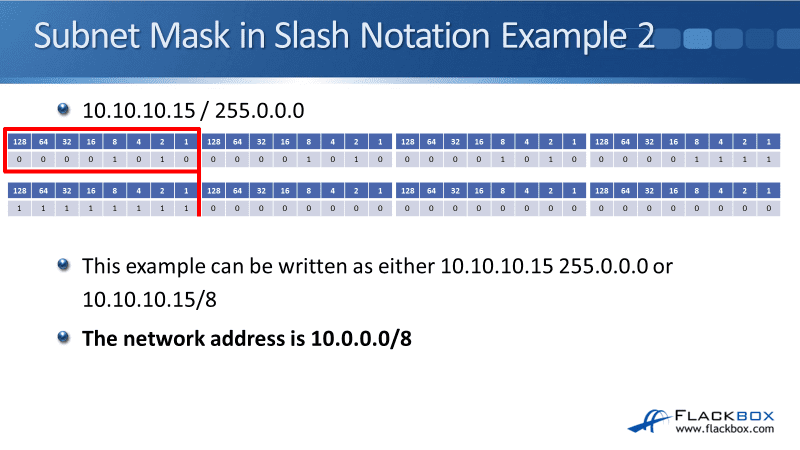
When we write this out, it’s just the network portion of the address that we specify. It’s a /8, so it’s only the first octet that includes the network portion, so that is the 10. All the rest of the address, the last three octets is the host portion.
When we write this address, it would be 10.0.0.0/8, and the available addresses would be 10.0.0.1 for our first host. The last host would be 10.255.255.254. We can’t use 10.255.255.255 because that would be the broadcast address, and 10.0.0.0 is the network address.
Additional Resources
Subnet Mask: https://study-ccna.com/subnet-mask/
Configure IP Addresses and Unique Subnets for New Users: https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13788-3.html
About Slash Notation: https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/overview/networksecurity/slash_about_c.html
Subnetting Practice Questions: https://www.flackbox.com/subnetting-practice-questions







