CCNA 200-301 (New CCNA)

All New CISCO 200-301 EXAM lessons and review question answers. Pearson New and Authentic E-books and publication for you to pass out 200-301 CCNA exam
Cisco certification changed all the way to its New format from 24th February 2020. if you have got some certifications before that, it will be converted to the new certification CCNA 200-301. The exam covers networking and security fundamentals, as well as automation and programmability. you only have to take one exam, the Cisco Certified Network Associate (200-301 CCNA), to earn the new CCNA!
Before february 24th There are following certifications were in practice but now all are merged to the new and a single certification New CCNA (200-301)
- CCNA Cloud
- CCNA Collaboration
- CCNA Data Center
- CCDA
- CCNA Industrial
- CCNA Routing and Switching
- CCNA Security
- CCNA Service Provider
- CCNA Wireless

With this major change, after passing CCNA 200-301 you can opt for the further specializations.
Pearson has Provided many Authentic and Original exam Preparation Guides, Practice tests, and Video Trainings. you can select from the following Guides all from Cisco Press.

CCNA 200-301 Network Simulator. The CCNA 200-301 Network Simulator is a single-user software package. It helps users develop and improve hands-on configuration and troubleshooting skills without the investment in expensive lab hardware. This state-of-the-art, interactive simulation software enables you to practice your networking skills with hundreds of structured labs designed to help you learn by doing, the most effective method of learning. Get Here
Lets start learning cisco 200-301 exam lessons…
This is going to be the first section of our CCNA video track. And it’s going to be investigating and exploring the functions of networking. So what are all the components that make up our networks? And we’re also going to be comparing and contrasting the physical and the logical typologies.
So when we look at the physical topologies, how are all of our devices connected to one another? And what are some of the speeds of the links that we’re using between some of those networks?
At the most basic level, a “network” is defined as a group of systems interconnected to share resources. You can find examples of such systems and resources in a social network to share work experience or personal events or a computer network to share file storage, printer access, or internet connectivity. cisco 200-301.
A network connects computers, mobile phones, peripherals, and even IoT (Internet of Things) devices. Switches, routers, and wireless access points (APs) are the essential networking basics. Through them, devices connected to your network can communicate with one another and with other networks, such as the Internet, which is a global system of interconnected computer networks.

Networks carry data in many types of environments, including homes, small businesses, and large enterprises. Large enterprise networks may have several locations that need to communicate with each other. You can use a network in your home office to communicate via the Internet to locate information, place orders for merchandise, and send messages to friends. You can also have a small office that is set up with a network that connects other computers and printers in the office.
Similarly, you can work in a large enterprise with many computers, printers, storage devices, and servers running applications that are used to communicate, store, and process information from many departments over large geographic areas.
CCNA 200-301 Official Cert Guide Library by Cisco Press. Part of the Official Cert Guide series. Cisco Press has the only study guides approved by Cisco for the new CCNA certification. The new edition of the best-selling two-book value-priced CCNA 200-301 Official Cert Guide Library includes updated content, new online practice exercises, more than 600 practice exam questions, and more than 2 hours of video training–PLUS the CCNA Network Simulator Lite Editions with 34 free Network Simulator labs (available via download on the companion web site). Get Here

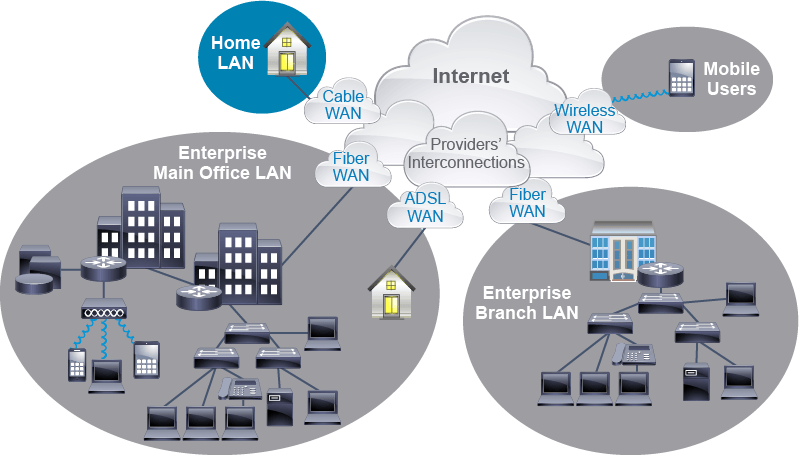
A network of computers and other components that are located relatively close together in a limited area is often referred to as a Local Area Network (LAN). Every LAN has specific components, including hardware, interconnections, and software. Wide Area Network (WAN) communication occurs between geographically separated areas and it’s typically provided by different telecommunication providers using various technologies using different media such as fiber, copper, cable, Asymmetric Digital Subscriber Line (ADSL), or wireless links. In enterprise internetworks, WANs connect the main office, branches, Small Office Home Office (SOHO), and mobile users.
As someone who is exploring the functions of networking, there are some important skills that you will build upon:
- Explain the functions, characteristics, and common components of a network.
- Read a network diagram, including comparing and contrasting the logical and physical topologies.
- Describe the impact of user applications on the network.

CCNA 200-301 Official Cert Guide, Volume 2. Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. It is built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. This book, combined with the CCNA 200-301 Official Cert Guide Volume 1, cover all of exam topics on the CCNA 200-301 exam. Get Here
In this section, we are focusing in on some of the basics to a network. We have two main things that we’re pointing out on this particular slide. The first thing is our local area network. These are all of the devices that are within close proximity to each other, like our routers and our switches and all of the end-user devices that those routers and switches will be connecting.
Now, we also have a branch office, or a remote local area network, which is, many times, what larger organizations that are geographically spread across are going to have. So our headquarters office might be in Chicago, and our remote branch office might be in Miami.
Now, we’re going to need to be able to leverage something such as a Wide Area Network, or a WAN connection, to be able to bridge those remote offices to the headquarters office. We see a couple different flavors or mechanisms, styles of WAN, fiber, asynchronous DSL. We’ll touch over those a little later in the class. cisco 200-301
And we’ll also see that sometimes we might have mobile users. Many times, those mobile users are also just going to be remote workers. Whether we work from home or we work from the road, we’ll be leveraging things like the internet to be able to connect to our enterprise campus.
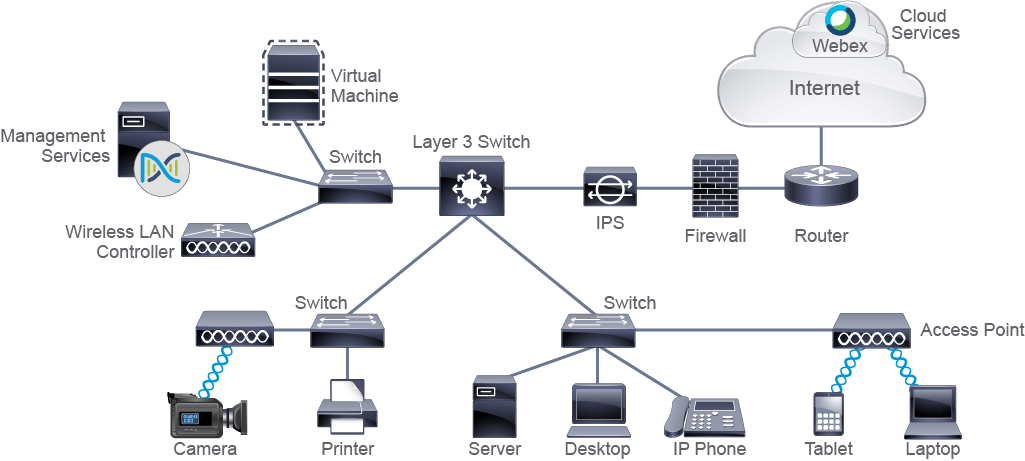
Now, when we kind of dial in or focus in on that enterprise campus, we can see we have a couple different tiers. The first tier is going to be our access layer. This is usually where those end users are going to connect to the network. So they can be connecting via a switch, or they can be connecting via an access point.
When we also look at things like the core, the core is going to have things like our routers, our core switches, or our multilayer switches. We’ll touch on those. And we might even have a data center on site as well.
Now, when we kind of look at some of the icons that we’ll be focusing in on all throughout the course, we’re going to have a layer-3 switch. Sometimes this is also referred to as a multilayer switch. Now, if you’re not too familiar with what layer 2 is versus layer 3, we’ll spend some time talking about the OSI model. And the OSI model is just a way for us to be able to distinguish between different technologies and different types of traffic.
So at layer 3, we’re usually routing or making a forwarding decision based on IP address, where a traditional switch is a layer-2 switch that can make forwarding decisions based on MAC address. We’ll go over this all again in case you’re brand new to this. Don’t worry. We’ll break it down even deeper a little bit later.
Here’s our icon for our router. And we also have things like an IPS or a firewall or things like a virtual machine or wireless LAN controller. But the big ones I really want you guys to focus in on at the moment is that layer-3 switch icon, that layer-2 switch icon, and that router.
Now, we also have some endpoints. Of course, these are the devices that we are going to be connecting to the network. So end-user devices are, of course, things like our IP-enabled phones or things like a virtual server or a laptop. And then when we look at those intermediate devices, these are many times the items that we just took a look at, in addition to things like that WLC, or that Wireless LAN Controller, maybe some security items.
As far as the different types of media that we’re using to connect these devices to our network, obviously wireless devices, like tablets and phones, are going to be using wireless. So when we look at our diagrams or our typologies, that’s going to be the icon for wireless connectivity. Serial links many times correlate with our wide area networks. Ethernet links can sometimes vary in speed, but this is just a simple, easy icon to display a physical connection between devices within our local area network.
We’ll spend a little bit of time later talking about services. And we’ll also break down some of the different types of applications that we find within our network.
CCNA 200-301 Official Cert Guide, Volume 1. Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. This book, combined with the CCNA 200-301 Official Cert Guide Volume 2, cover all of exam topics on the CCNA 200-301 exam. Get Here

The term network is used in many different arenas. Examples of networks are social networks, phone networks, television networks, neural networks, and, of course, computer networks. A network is a system of connected elements that operate together. A computer network connects personal computers (PCs), printers, servers, phones, cameras, and other types of devices. A computer network connects devices in a way allowing them to exchange data among each other, which facilitates information and resource sharing. At home, computers allow family members to share files (such as photos) and print documents on a network printer, televisions can play movies or other media stored on your computers, and internet-enabled devices can connect to webpages, applications and services anywhere in the world.
In the business environment you have a lot of business operations – marketing, sales, and IT. You need to develop apps that allow information to be collected and processed. Computer systems that collect and process the information need to communicate with each other in order to share resources. You also need an infrastructure that supports employees, who need to access these resources and interact with each other. A network allows multiple devices such as laptops, mobile devices, servers, and shared storage to exchange information with each other. There are various components, connected to each other that are necessary for this communication to take place. This infrastructure allows a business to run, lets customers to connect to the business (either through salespeople or through an online store) and allows a business to sell its products or services. To run normally, at the end of the day, a business and its applications relies on networking technology.
A computer network can exist on its own, independent of other computer networks. It can also connect to other networks. The internet is an example of many networks interconnected together. It is global in its span and scope. To operate successfully, interconnected networks follow standardized rules to communicate. These rules are accepted and adhered to by each participating network.
The early internet-connected only several mainframe computers with computer terminals. The mainframe computers were large and their computing power was considered enormous (albeit being the equivalent to today’s mobile phone). Terminals were simple and inexpensive devices, which were used only to input data and display the results. Teletype is an example of such a device. The range of devices that connects to the internet has expanded in the last decades. The internet now connects not only laptops, smartphones, and tablets but also game consoles, television sets, home systems, medical monitors, home appliances, thunder detectors, environment sensors, and many more things. The earlier concept of centralized computing resources is revived today in the form of computing clouds.

Computer network engineers are people who design, develop, and maintain highly available network infrastructure to support the information technology activities of the business. Network engineers interact with users of the network and provide support or consultancy services about design and/or network optimization. Network engineers typically have more knowledge and experience than network technicians, operators, and administrators. A network engineer should update their knowledge of networking constantly to keep up with new trends and practices.
Users who wish to connect their networks to the internet acquire access through a service provider’s access network. Service providers’ networks can use different technologies from dial-up or broad-band telephony networks, such as ADSL network, cable networks, mobile, radio, or fiber optic networks.
A service provider network can cover large geographical areas. Service provider networks also maintain connections between themselves and other service providers to enable global coverage.
Computer networks can be classified in several ways, which can be combined to find the most appropriate one for the implementation. Local and remote networks are distinguished by the distance between the user and the computer networks the user is accessing. cisco 200-301
Examples of networks categorized by their purpose would be the data center network and storage area network (SAN). Focusing on the technology used, you can distinguish wireless or wired networks. Looking at the size of the network in terms of the number of devices it has, there are small networks, usually with less than 10 devices, medium to large networks consisting of tens to hundreds of devices, and very large, global networks, such as the internet, which connects thousands of devices across the world.
One of the most common categorizations looks at the geographical scope of the network. Within it, there are local-area networks (LANs) that connect devices located relatively close together in a limited area. Contrasting LANs, there are wide-area networks (WANs), which cover broad geographic area and are managed by service providers.
An example of a LAN network is a university campus network that can span several collocated buildings. An example of a WAN would be a telecommunication provider’s network that interconnects multiple cities and states. This categorization also includes metropolitan-area networks (MANs), which span a physical area larger than LAN but smaller than WAN, for instance, a city.

medium-to-large enterprise networks can span multiple locations. Usually, they have a main office or Enterprise Campus, which holds most of the corporate resources, and remote sites, such as branch offices or home offices of remote workers.
A home office usually has a small number of devices and is called the Small Office/Home Office (SOHO). SOHO networks mostly use the internet to connect to the main office. The main office network, which is a LAN in terms of its geographical span, may consist of several networks that occupy many floors or it may cover a campus that contains several buildings. Many corporate environments require the deployment of wireless networks on a large scale and they use Wireless LAN Controllers (WLC) for centralizing management of wireless deployments.
Enterprise Campuses also typically include a separate Data Center which is home to the computational power, storage, and applications necessary to support an enterprise business. Enterprises are also connected to the internet and internet connectivity is protected by a firewall. Branch offices have their own LANs with their own resources, such as printers and servers, and may store corporate information, but their operations largely depend on the main office, hence the network connection with it. They connect to the main office by a WAN or internet using routers as gateways.

CCNA 200-301 Official Cert Guide Library Premium Edition eBook and Practice Test. Cisco Press has the only study guides approved by Cisco for the new CCNA certification. The new edition of the best-selling two-book, value-priced CCNA 200-301 Official Cert Guide Library includes updated content, new online practice exercises, more than 400 practice exam questions, and more than 2 hours of video training–PLUS the CCNA Network Simulator Lite Editions with 34 free Network Simulator labs (available on the companion website). Get Here

Networks support the activities of many businesses and organizations and are required to be secure, resilient and to allow growth. The design of a network requires considerable technical knowledge.
Network engineers commonly use validated network architecture models to assist in the design and the implementation of the network. Examples of validated models are Cisco three-tier hierarchical network architecture model, spine-leaf model, and Cisco Enterprise Architecture model.
These models provide hierarchical structure to Enterprise networks, which is used to design the network architecture in a form of layers (for example LAN Access, LAN Core), with each layer providing different functionalities.
Note
The words internet and web are very often used interchangeably, but they do not share the same meaning. The internet is a global network that interconnects many networks and therefore provides a world-wide communication infrastructure.
The World Wide Web describes one way to provide and access information over the internet using a web browser. It is a service that relies on connections provided by the internet for its function.
All the exchange of data within the internet follows the same well-defined rules, called protocols, which are designed specifically for internet communication. These protocols specify, among other things, the usage of hyperlinks and Uniform Resource Identifiers (URIs). The internet is a base for many other data exchange services, such as e-mail or file transfer.
It is a common global infrastructure, composed of many computer networks connected together that follow communication rules standardized for the internet. The protocols and processes of the internet are defined by a set of documents called Request for Comments (RFCs).
CCNA 200-301 Official Cert Guide, Volume 2 Premium Edition eBook and Practice Test. The exciting new CCNA 200-301 Official Cert Guide, Volume 2, Premium Edition eBook and Practice Test is a digital-only certification preparation product combining an eBook with enhanced Pearson Test Prep Practice Test. This eBook, combined with CCNA 200-301 Official Cert Guide, Volume 1, cover all the exam topics on the CCNA 200-301 exam. Get Here

Q&A
Question
An employee has the option of working from home, and their home is located in the same town as the main office. The only option available to connect to the main office is to use the internet. The employee sets up the network, consisting of one desktop computer and a printer. Which statements regarding the worker’s SOHO are correct? (Choose two.)
- The SOHO network is integral to the main office network.
- The SOHO network is an individual network that can function on its own.
- The SOHO network devices, such as the desktop computer and a printer, must be connected to the internet to communicate.
- SOHO needs a connection to the internet to access the enterprise resources located at the main office.
- The SOHO is considered by the main office to be a local destination.
Answer
The correct answers are “The SOHO network is an individual network that can function on its own” and “SOHO needs a connection to the internet to access the enterprise resources located at the main office.” Although located in the same town, the home office is not and integral part of the main office LAN network. It can be considered a part of the overall enterprise network. When a remote worker needs to access enterprise resources, they need to connect to the main office network, in this case, via the internet. For entertainment and nonwork related activities, the SOHO network functions without having to connect to the main office. No internet connection is required for the devices within the home office to communicate with each other.

CCNA 200-301 Official Cert Guide, Volume 1 Premium Edition eBook and Practice Test. Premium Edition eBook and Practice Test is a digital-only certification preparation product combining an eBook with enhanced Pearson Test Prep Practice Test. This book, combined with the CCNA 200-301 Official Cert Guide Volume 2, cover all of exam topics on the CCNA 200-301 exam. Get Here
Exploring the Functions of Networking
Components of a Network
A network can be as simple as two PCs that are connected by a wire or as complex as several thousand devices that are connected through different types of media. The elements that form a network can be roughly divided into 3 categories: devices, media, and services. Devices are interconnected by media. Media provides the channel over which the data travels from source to destination. Services are software and processes that support common networking applications in use today.
Network Devices
Devices can be further divided into endpoints and intermediary devices
Endpoints: End devices, which are most common to people, fall into the category of endpoints. In the context of a network, end devices are called end-user devices, and include PCs, laptops, tablets, mobile phones, game consoles, and television sets.
Endpoints are also file servers, printers, sensors, cameras, manufacturing robots, smart home components, and so on. At the beginning of computer networking, all end devices were physical hardware units. Today, many end devices are virtualized, meaning that they do not exist as separate hardware units any more.
In virtualization, one physical device is used to emulate multiple end devices, for example all the hardware components that one end device would require. The emulated computer system operates as if it were a separate physical unit and has its own operating system and other required software.
In a way, it behaves like a tenant living inside a host physical device, using its resources (processor power, memory, and network interface capabilities) to perform its functions. Virtualization is commonly applied for servers to optimize resource utilization, as server resources are often underutilized when they are implemented as separate physical units.
Intermediary devices: These devices interconnect end devices or interconnect networks. In doing so, they perform different functions, which include regenerating and retransmitting signals, choosing the best paths between networks, classifying and forwarding data according to priorities, filtering traffic to allow or deny it based on security settings, and so on.
As endpoints can be virtualized, so can intermediary devices or even entire networks. The concept is the same as in the endpoint virtualization—the virtualized element uses a subset of resources available at the physical host system. Intermediary devices that are commonly found in enterprise networks are:
Switches: These devices enable multiple endpoints such as PCs, file servers, printers, sensors, cameras, and manufacturing robots to connect to the network. Switches are used to allow devices to communicate on the same network. In general, a switch or group of interconnected switches attempt to forward messages from the sender so it is only received by the destination device. cisco 200-301
Usually, all the devices that connect to a single switch or a group of interconnected switches belong to a common network and can, therefore, communicate directly with each other. If an end device wants to communicate with a device that is on a different network, then it requires “services” of a device that is known as a router, which connects different networks together.

Routers: These devices connect networks and intelligently choose the best paths between networks. Their main function is to route traffic from one network to another. For example, you need a router to connect your office network to the internet.
An analogy that may help you understand the basic function of switches and routers is to imagine a network as a neighborhood. A switch is a street that connects the houses, and routers are the crossroads of those streets. The crossroads contain helpful information such as road signs, to help you in finding a destination address.
Sometimes, you might need the destination after just one crossroad, but other times you might need to cross several. The same is true in networking. Data sometimes “stops” at several routers, before it is delivered to the final recipient. Certain switches combine functionalities of routers and switches and they are called Layer 3 switches.
- APs: These devices allow wireless devices to connect to a wired network. An AP usually connects to a switch as a standalone device, but it also can be an integral component of the router itself.
- WLCs: These devices are used by network administrators or network operations centers to facilitate the management of many APs. The WLC automatically manages the configuration of wireless APs.
Next-generation firewalls (NGFW): Firewalls are network security systems that monitor and control the incoming and outgoing network traffic based on predetermined security rules.
A firewall typically establishes a barrier between a trusted, secure internal network, and another outside network, such as the internet, that is assumed not to be secure or trusted. The term next-generation firewall indicates a firewall that provides additional features to accommodate the newest security requirements.
An example of such a feature is the ability to recognize user applications, for instance, a game running inside an application, such as a browser, that is connected to Facebook.
Intrusion Protection System (IPS): An IPS is a system that performs deep analysis of network traffic, searching for signs that behavior is suspicious or malicious. If the IPS detects such behavior, it can take protective action immediately. An IPS and a firewall can work in conjunction to defend a network.
Management Services: A modern management service offers centralized management that facilitates designing, provisioning, and applying policies across a network. It includes features for discovery and management of network inventory, management of software images, device configuration automation, network diagnostics, and policy configuration. It provides end-to-end network visibility and uses network insights to optimize the network. An example of such centralized management service is Cisco DNA Center.
In user homes, you can often find one device that provides connectivity for wired devices, provides connectivity for wireless devices, and provides access to the Internet. You may be wondering which kind of device it is. It has characteristics of a switch in that it provides physical ports to plug local devices, a router, as it enables users to access other networks and the internet, and a WLAN AP, as it allows wireless devices to connect to it. It is actually all three of these devices in a single package. This device is often called a wireless router.
Another example of a network device is a file server, which is an end device. A file server runs software that implements protocols that are standardized to support file transfer from one device to another over a network.
This service can be implemented by either File Transfer Protocol (FTP) or Trivial File Transfer Protocol (TFTP). Having an FTP or TFTP server in a network allows uploads and downloads of files over the network. An FTP or TFTP server is often used to store back-up copies of files that are important to network operation, such as operating system images and configuration files. Having those files in one place makes file management and maintenance easier.
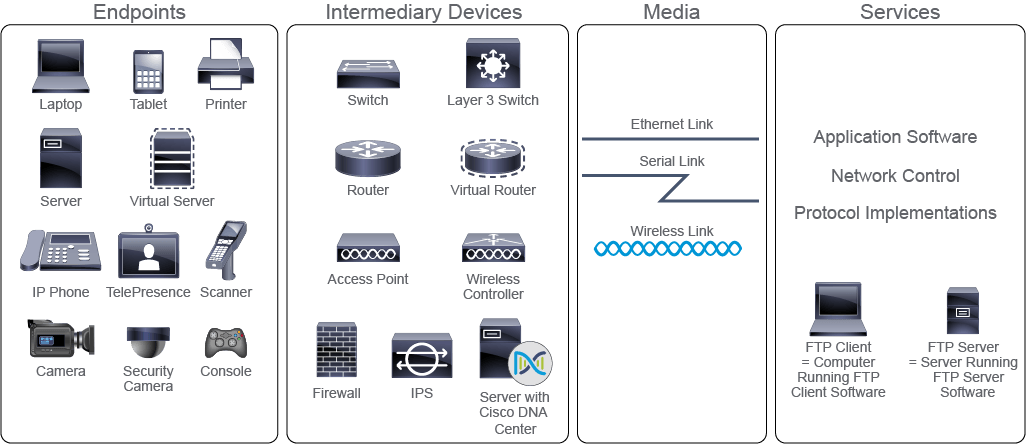
Media
Media are the physical elements that connect network devices. Media carry electromagnetic signals that represent data. Depending on the medium, electromagnetic signals can be guided, like in wires and fiber optic cables, or can be propagated, like in wireless transmissions, such as are WiFi, mobile, and satellite.
Different media have different characteristics and the selection of the most appropriate medium would depend on the circumstances, such as the environment in which the media is used, distances that need to be covered, availability of financial resources, and so on. For instance, for a filming crew working in a desert, a satellite connection (air medium) might be the only available option.
Connecting of wired media to network devices is greatly eased by the use of connectors. A connector is a plug, which is attached to each end of the cable. The most common type of connector on a LAN is the plug that looks like an analog phone connector. It is called a registered jack-45 (RJ-45) connector.
To be able to connect the media, which connects a device to a network, devices use network interface cards (NICs). The media “plugs” directly into the NIC. NICs translate the data that is created by the device into a format that can be transmitted over the media.
NICs used on LANs are also called LAN adapters. End devices used in LANs usually come with several types of NICs installed, such as wireless NICs and Ethernet NICs. NICs on a LAN are uniquely identified by a Media Access Control (MAC) address.
The MAC address is hard-coded or “burned in” by the NIC manufacturer. NICs that are used to interface with WANs are called WAN interface cards (WICs) and they use serial links to connect to a WAN network.
Network Services
Services in a network comprise software and processes that implement common network applications, such as email and web, also including the less obvious processes, implemented across the network, all of which generate data and determine how data is moved through the network
Companies typically centralize business-critical data and applications into central locations called Data Centers. These data centers can include routers, switches, firewalls, storage systems, servers, and application delivery controllers.
Similar to Data Center centralization, computing resources can also be centralized off-premises in the form of a cloud. Clouds can be private, public, or hybrid, and aggregate the computing, storage, network, and application resources in central locations. Cloud computing resources are configurable and shared among many end-users.
The resources are transparently available, regardless of the user point of entry (a personal computer at home, an office computer at work, a smartphone or tablet, or a computer on a school campus). Data stored by the user is available whenever the user is connected to the cloud.

Question
Which four of the following are network intermediary devices? (Choose four.)
- tablet
- temperature sensor
- access point
- firewall
- laptop
- switch
- file server
- wireless LAN controller
Answer
The correct answers are “access point,” “firewall,” “switch,” and “wireless LAN controller.” Tablets, laptops, sensors, and file servers do not interconnect devices or networks, therefore they are not intermediary devices. Tablets, laptops, temperature sensors, and file servers are examples of network end-devices.

CCNA 200-301 Foundations LiveLessons: A Pre-CCNA Review of Networking Fundamentals (Video Training). Even though the CCNA certification is an associate level program, exam candidates are expected to have a basic knowledge of IP addressing, knowledge of networking fundamentals, and some experience deploying and managing Cisco solutions. CCNA 200-301 Foundations LiveLessons provides you with the pre-requisite knowledge needed to begin your CCNA exam preparation. Assuming no previous knowledge, this comprehensive networking fundamentals course covers the theory and operation of multiple networking technologies, all designed to lay a strong foundation for your CCNA studies and beyond. Get Here
Characteristics of a Network
When you purchase a mobile phone or a PC, the specifications list tells you the important characteristics of the device, just as specific characteristics of a network help describe its performance and structure. When you understand what each characteristic of a network means, you can better understand how the network is designed, how it performs, and which aspects you may need to adjust to meet user expectations.
You can describe the qualities and features of a network by considering these characteristics:
- Topology: A network topology is the arrangement of its elements. Topologies give insight into physical connections and data flows among devices. In a carefully designed network, data flows are optimized and the network performs as desired.
- Bitrate or Bandwidth: Bitrate is a measure of the data rate in bits per second of a given link in the network. The unit of bitrate is bit per second (bps). This measure is often referred to as bandwidth, or speed in device configurations, which is sometimes thought of as speed. However, it is not about how fast 1 bit is transmitted over a link—which is determined by the physical properties of the medium that propagates the signal—it is about the number of bits transmitted in a second. Link bitrates commonly encountered today are one and 10 Gigabits per second (1 or 10 billion bits per second). 100-Gbps links are not uncommon either.
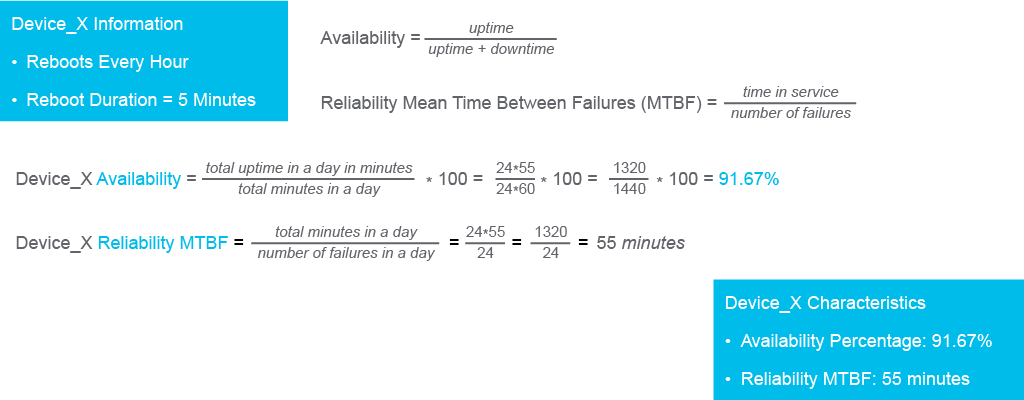
- Availability: Availability indicates how much time a network is accessible and operational. Availability is expressed in terms of the percentage of time the network is operational. This percentage is calculated as a ratio of the time in minutes that the network is actually available and the total number of minutes over an agreed period, multiplied by 100. In other words, availability is the ratio of uptime and total time, expressed in percentage. To ensure high availability, networks should be designed to limit the impact of failures and to allow quick recovery when a failure does occur. High availability design usually incorporates redundancy. The redundant design includes extra elements, which serve as back-ups to the primary elements and take over the functionality if the primary element fails. Examples include redundant links, components, and devices.
- Reliability: Reliability indicates how well the network operates. It considers the ability of a network to operate without failures and with the intended performance for a specified time period. In other words, it tells you how much you can count on the network to operate as you expect it to. For a network to be reliable, the reliability of all its components should be considered. Highly reliable networks are highly available, but a highly available network might not be highly reliable—its components might operate but at lower performance levels. A common measure of reliability is the mean time between failures (MTBF), which is calculated as the ratio between the total time in service and the number of failures, were not meeting the required performance level is considered a failure. Choosing highly reliable redundant components in the network design increases both availability and reliability.
For instance, let’s consider a networking device that reboots every hour. The reboot takes 5 minutes, after which the device works as expected. The figure shows the calculations of availability and reliability.
The availability percentage for the period of one day can be calculated as follows:
- Scalability: Scalability indicates how easily the network can accommodate more users and data transmission requirements, without affecting current network performance. If you design and optimize a network only for the current requirements, it can be very expensive and difficult to meet new needs when the network grows.
- Security: Security tells you how well the network is defended from potential threats. Both network infrastructure and the information that is transmitted over the network should be secured. The subject of security is important, and defense techniques and practices are constantly evolving. You should consider security whenever you take actions that affect the network.
- Quality of Service (QoS): QoS includes tools, mechanisms, and architectures, which allow you to control how and when network resources are used by applications. QoS is especially important for prioritizing traffic when the network is congested.
- Cost: Cost indicates the general expense for the initial purchase of the network components, and any costs associated with the installation and ongoing maintenance of these components.
- Virtualization: Traditionally, network services and functions have only been provided via hardware. Network virtualization creates a software solution which emulates network services and functions. Virtualization solves a lot of the networking challenges in today’s networks, helping organizations centrally automate and provision the network from a central management point.
These characteristics and attributes provide a means to compare various networking solutions.
Content Review Question
Which three statements about network characteristics are true? (Choose three.)
- Bitrate is a measure of the data rate in bits per second of a given link in the network.
- Scalability indicates how many devices there are currently on the network.
- QoS tells you how well the network is defended from potential threats.
- Availability is a measure of the probability that the network will be available for use when it is required.
- Reliability indicates to what extent you can count upon network components to perform as they are expected to.
Answer
The correct answers are “Bitrate is a measure of the data rate in bits per second of a given link in the network,” “Availability is a measure of the probability that the network will be available for use when it is required,” and “Reliability indicates the dependability of the components that make up the network.” The physical, not the logical, topology depicts the arrangement of cables, devices, and end systems. Scalability is not concerned with the current count of network elements, only with its capability to grow without disturbances. QoS tells you how well a network supports business operations, especially in the case of congestions, while the security tells how well the network is defended from potential threats.

CCNA 200-301 Exam Cram, 6th Edition. CCNA 200-301 Exam Cram, Sixth Edition is the perfect study guide to help you pass the Cisco 200-301 CCNA exam, providing coverage and practice questions for every exam topic. The book contains an extensive set of preparation tools, including topic overviews, exam alerts, CramSavers, CramQuizzes, chapter-ending review questions, author notes and tips, Packet Tracer labs, and an extensive glossary. Get Here
Physical vs. Logical Topologies
In this topic, we’re going to compare and contrast physical and logical topologies. First we’re going to focus in on our physical topologies. When we look at the bus, let’s say, for example, if we had any sort of break in the link or in the cable between the devices, we would lose communication. So there was no resiliency or redundancy.
With a ring topology, we had a very simple topology, where if there was a break, we may only be able to communicate in the opposite direction. Sometimes they would implement an additional ring for additional redundancy. But we’d only be as fast as those two links combined.
Now, star and mesh are more the commonly seen topologies today. And when we think about those two topologies, the first star, which is sometimes also known as hub and spoke, is many times something that we’re going to see in a wide area network. So the center of the star might be headquarters, and the endpoints are going to be our branch offices. Or in other words, when we think about how those branch offices do not connect with one another, we’ll see that branch router one and branch router two have to go through headquarters in order to communicate with one another. So this sometimes is a less expensive way if you need to scale to, let’s say, 50 or 100 branch offices.
Now, as far as the mesh topology, this, many times, is what we see within a traditional local area network, where every switch is connected to every switch. Full mesh, and we have some redundancy in our routers. And we might see something like a partial mesh over a WAN technology. So that’s what they’re pointing out here, where not every device is connected to every remote device. If we did have every single connection, that would be the full mesh.
Now, of course, the full mesh, you’re going to see a higher price point in order to aggregate every remote site, if that was a WAN technology, where the partial might come in at a little bit of a lower price point because not every device is connected to one another. Now, as far as logical topologies go, this is really the flow of the traffic. So here what we’re looking at is a user in the blue VLAN. And he might need to get routed to the green VLAN, that server up there.
So where’s the traffic actually traversing the network? Now, the router does his look up. He realizes that it’s going to be forwarded to this green VLAN over here. And that’s the flow of traffic. If we implemented, let’s say, another switch somewhere in here– let’s say we had a switch over here– and then the original flow of traffic, there was a break in the link. Then we would converge, and we would find another path to the destination.
So some organizations may not necessarily have a logical topology. But as administrators, it is good or important to have a general idea of where the flow of the traffic is going along your environment. Now, a lot of the things that the bottom here we already looked at– the switch, the laptop icons, all that good stuff. But some of the other items in a topology or network diagram that we focus in up at the top here might be things like the speed of the interfaces– so are we doing 100 Mb or fast ethernet from the endpoints up to the switches? Or are we doing gig connections between switches and routers or 10 gigs between those multi-layer switches– and so on and so forth.
So keep an eye out sometimes for those. We also might see just the IP addresses for the different LAN segments. So here we see the 192.168.1.0 subnet with a slash 24 subnet mask. And we also see, just from a really high level, some of the pieces that might be put together, like the WAN circuits. Or we might see a firewall or an IPS somewhere else in our environment.
Now, as far as how different applications have an impact on the network, we’re going to see that, typically, things like traditional data traffic is not necessarily very sensitive to any types of changes in the network. So in other words, if there’s any drops or delays, traditional data can be retransmitted. And so it many times, by default, is bursty. And it’s not always smooth.
But with voice and video, we typically want things that are smooth and that are going to be sensitive to drops and delays. So this is going to tie into a concept called Quality of Service, or QoS. It’s a way for us to be able to identify these different types of applications and say, hey, when there’s a traffic jam on the network, let’s make sure that this traffic gets expedited before the rest of the vehicles or the rest of the flow of traffic.
So we’ll touch a little bit later on things like latency and loss and bandwidth. But these are some of the things that will affect voice and video. And so we do have some necessary requirements for those applications. And when we think about traditional batch applications, like FTP or file transfer protocol, it uses transmission control protocol, or TCP. So we constantly have this bi-directional communication. So if there’s a few packets that get dropped along the way, the sender can always retransmit those dropped packets.

And interactive applications are many times going to need a little bit better response times. And the bandwidth is usually important for things like databases. But really, what, again, we kind of, sort of, emphasized on the previous slide with Quality of Service, is that those real-time applications are voice over IP implementations, any type of video over IP. These have to have– we have to have low latency, and we have to be sure that the packet loss is very, very minimal in order to make sure that every single packet gets to the destination because we aren’t going to retransmit.
And usually, things like UDP, they’re going to have a much smaller header versus TCP has a much bigger header. So these tiny little UDP messages are going to get sent across the wire a little bit more efficiently. So hopefully, that gave you guys a little bit of an idea of some of the different applications and how they are affected over the network.
Each network has both a physicaland a logical topology. The physical topology of a network refers to the physical layout of the devices and cabling. The term node is commonly used when discussing topology diagrams. For networking topology diagrams, a node is a device.
Two networks might have the same physical topology, but distances between nodes, physical interconnections, transmission rates, or signal types may be different. A physical topology must be implemented using media that is appropriate for it. In wired networks, recognizing the type of cabling used is important in describing the physical topology. The figure represents some of the physical topologies that you may encounter.
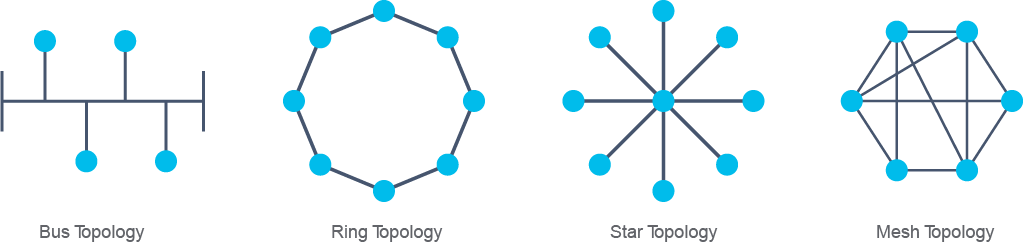
The following are the primary physical topology categories:
- Bus: In a bus topology, every workstation is connected to a common transmission medium, a single cable, which is called a backbone or bus. Therefore, each workstation is directly connected to every other workstation in the network. In early bus topologies, computers and other network devices were connected to a central coaxial cable via connectors.
- Ring: In a ring topology, computers and other network devices are cabled in succession and the last device is connected to the first one to form a circle or ring. Each device is connected to exactly two neighbors and has no direct connection to a third. When one node sends data to another, the data passes through each node that lies between them until it reaches the destination.
- Star: The most common physical topology is a star topology. In this topology, there is a central device to which all other network devices connect via point-to-point links. This topology is also called the hub and spoke topology. There are no direct physical connections among spoke devices. This topology includes star and extended star topologies. In an extended star topology, one or more spoke devices is replaced by a device that has its own spokes. In other words, it is composed of multiple star topologies, whose central devices are connected between each other.
- Mesh: In a mesh topology, a device can be connected to more than one other device. For one node to reach others there are multiple paths available. Redundant links increase reliability and self-healing. In a full mesh topology, every node is connected to every other node. In partial mesh, certain nodes do not have connections to all other nodes.
The logical topology is the path along which data travels from one point in the network to another. The diagram depicts the logical topology between PC A and the Server. In this example, data does not follow the shortest physical path, which would go through two switches. The logical topology requires data to also travel through the router in order for the two devices to communicate. The same could be true for all other end devices. Logical topology would then be a star, where the router is a central device.
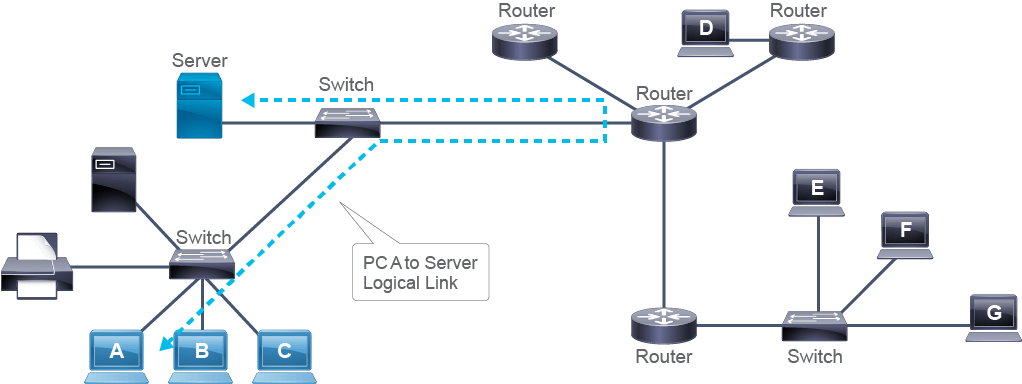
It is possible for the logical and physical topology of a network to be of the same type. However, physical and logical topologies often differ. For example, an Ethernet hub is a legacy device that functions as a central device to which other devices connect in a physical star. The characteristic of a hub is that it “copies” every signal received on one port to all other ports. So a signal sent from one node is received by all other nodes. This behavior is typical of a bus topology. Because data flow has the characteristics of a bus topology, it is a logical bus topology.
The logical topology is determined by the intermediary devices and the protocols chosen to implement the network. The intermediary devices and network protocols both determine how end devices access the media and how they exchange data.
A physical star topology in which a switch is the central device is by far the most common in implementations of LANs today. When using a switch to interconnect the devices, both the physical and the logical topologies are star topologies.
Content Review Question
Which physical topology is depicted in the diagram?
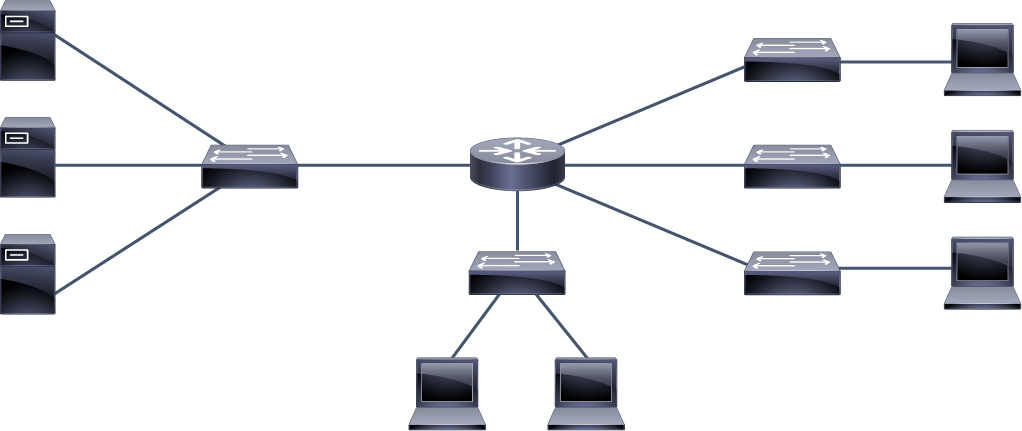
- bus
- ring
- mesh
- extended star
Answer
The correct answer is “extended star.” The central router could be considered the center of the star. Other devices connect to it. In the diagram, two switches (positioned to the left and under the router), connect multiple devices and each acts as a center of two smaller stars. In other words, tentacles of the router’s star are stars themselves, so the topology is an extended star.
CCNA 200-301 Exam Cram Premium Edition eBook and Practice Test, 6th Edition. The exciting CCNA 200-301 Exam Cram Premium Edition eBook and Practice Test is a digital-only certification preparation product combining an eBook with the powerful Pearson Test Prep practice test software. Get Here

Interpreting a Network Diagram
Network diagrams are visual aids in understanding how a network is designed and how it operates. In essence, they are maps of the network. They illustrate physical and logical devices and their interconnections. Depending on the amount of information you wish to present, you can have multiple diagrams for a network. Most common diagrams are physical and logical diagrams. Other diagrams used in networking are sequence diagrams, which illustrate the chronological exchange of messages between two or more devices.
Both physical and logical diagrams use icons to represent devices and media. Usually, there is additional information about devices, such as device names and models.
Physical diagrams focus on how physical interconnections are laid out and include device interface labels (to indicate the physical ports to which media is connected) and location identifiers (to indicate where devices can be found physically). Logical network diagrams also include encircling symbols (ovals, circles, and rectangles), which indicate how devices or cables are grouped. These symbols further include device and network logical identifiers, such as addresses. These symbols also indicate which networking processes are configured, such as routing protocols and provide their basic parameters.
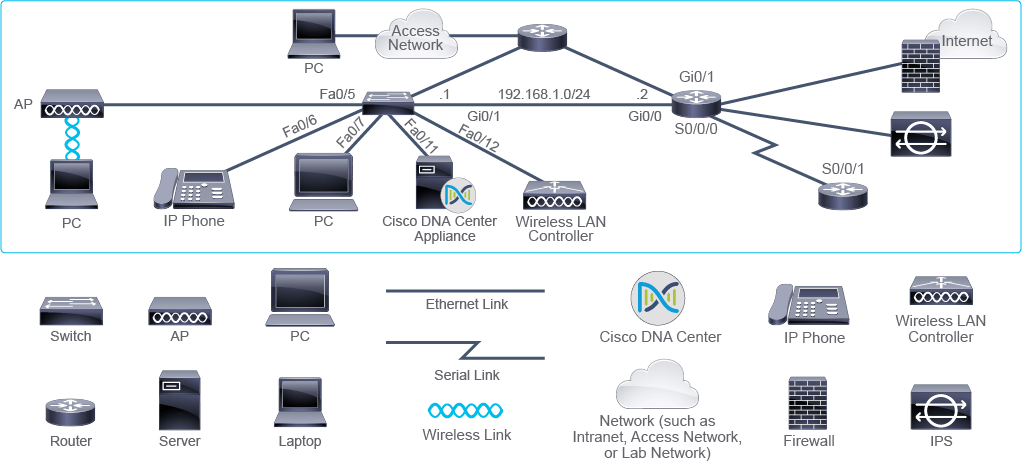
n the example, you can see interface labels” S0/0/0,” “Fa0/5,” and “Gi0/1.” The label is composed of letters followed by numbers. Letters indicate the type of an interface. In the example, “S” stands for Serial, “Fa” stands for Fast Ethernet, and “Gi” for Gigabit Ethernet.
Devices can have multiple interfaces of the same type. The exact position of the interface is indicated by the numbers that follow, which are subject to conventions. For instance, the label S0/0/0 indicates serial port 0 (the last zero in the label), in the interface card slot 0 (the second zero) in the module slot 0 (the first zero).
Note
The name Fast Ethernet indicates an Ethernet link with the speed of 100 Mbps.
The diagram also includes the Internet protocol version 4 (IPv4) address of the entire network given by 192.168.1.0/24. This number format indicates not only the network address, which is 192.168.1.0 but also the network’s prefix, a representation of its subnet mask, which is /24. IPv4 addresses of individual devices are shown as “.1” and “.2.” These numbers are only parts of the complete address, which is constructed by combining the address of the entire network with the number shown. The resulting address of the device in the diagram would be 192.168.1.1.
Question
Which interface is defined in the S0/0/0 format?
- Ethernet interface
- Gigabit Ethernet interface
- Serial interface
- FastEthernet interface
Answer
The correct answer is “serial interface.” The type of the interface is commonly identified by a letter: “S” is chosen to indicate a serial interface; “Fa” indicates a FastEthernet interface; “Gi” indicates a Gigabit Ethernet interface.
Question
Which two options represent the meaning of the label Gi2/1? (Choose two.)
- The interface is a Gigabit Ethernet interface.
- The interface is a FastEthernet interface.
- There is more than one slot for interface cards on the hardware.
- The device is a router.
- The cable that is connected to this interface is a copper cable.
Answer
The correct answers are “The interface is a Gigabit Ethernet interface” and “There is more than one slot for interface cards on the hardware.” The “G” letter in the “Gi” label signifies gigabit (a billion bits), which is the maximum speed of the interface. “Fa” letters would indicate a FastEthernet interface. Based on the interface label alone, you cannot tell what kind of device the interface is installed on nor what kind of cabling would be adequate for the port. This information is learned from the device specification. Both routers and switches can be equipped with Gigabit Ethernet interfaces.
Impact of User Applications on the Network
The data traffic that is flowing in a network can be generated by end-users or can be control traffic. Users generate traffic by using applications. Control traffic can be generated by intermediary devices or by activities related to the operation, administration, and management of the network. Today, users utilize many applications. The traffic created by these applications differs in its characteristics. Usage of applications can affect network performance and, in the same way, network performance can affect applications. Usage translates to the user’s perception of the quality of the provided service—in other words, a user experience that is good or bad. Recall that QoS is implemented to prioritize network traffic and maximize the user experience.
User applications can be classified to better describe their traffic characteristics and performance requirements. It is important to know what traffic is flowing in your network and describe the traffic in technical terms. An example of traffic types found in today’s network is given in the figure. This knowledge is used to optimize network design.
To classify applications, their traffic, and performance requirements are described in terms of these characteristics:
- Interactivity: Applications can be interactive or non-interactive. Interactivity presumes that a given request-response is expected for the normal functioning of the application. For interactive applications, it is important to evaluate how sensitive they are to delays—some might tolerate larger delays up to practical limits, but some might not.
- Real-time responsiveness: Real-time applications expect a timely serving of data. They are not necessarily interactive. An example of a real-time application is live football match video streaming (live streaming) or video conferencing. Real-time applications are sensitive to delay. Delay is sometimes used interchangeably with the term latency. Latency refers to the total amount of time from the source sending data to the destination receiving it. Latency accounts for propagation delay of signals through media, the time required for data processing on devices it crosses along the path, etc. Because of the changing network conditions, latency might vary during data exchange: some data might arrive with less latency than others. The variation in latency is called jitter.
- Amount of data generated: There are applications that produce a low quantity of data, such as voice applications. These applications do not require much bandwidth. Usually, they are referred to as bandwidth benign applications. On the other hand, video streaming applications produce a significant amount of traffic. This kind of application is also termed bandwidth greedy.
- Burstiness: Applications that always generate a consistent amount of data are referred to as smooth or non-bursty applications. On the other hand, bursty applications at times create a small amount of data, but they can change behavior for shorter periods. An example is web browsing. If you open a page in a browser that contains a lot of text, a small amount of data is transferred. But if you start downloading a huge file, the amount of data will increase during the download.
- Drop sensitivity: Packet loss is losing packets along the data path, which can severely degrade the application performance. Some real-time applications (such as Video On Demand) are sensitive to the perceived packet loss when using network resources. You can say that such applications are drop sensitive.
- Criticality to business: This aspect of an application is “subjective” in that it depends on someone’s estimate of how valuable and important the application is to a business. For instance, an enterprise that relies on video surveillance to secure its premises might consider video traffic as a top priority, while another enterprise might consider it totally irrelevant.

One way that applications can be classified is as follows:
- Batch applications: Applications such as FTP and TFTP are considered batch applications. Both are used to send and receive files. Typically, a user selects a group of files that need to be retrieved and then starts the transfer. Once the download starts, no additional human interaction is required. The amount of available bandwidth determines the speed at which the download occurs. While bandwidth is important for batch applications, it is not critical. Even with low bandwidth, the download is completed eventually. Their principal characteristics are:
- Typically do not require direct human interaction.
- Bandwidth important but not critical.
- Examples: FTP, TFTP, inventory updates.
- Interactive applications: Applications in which the user waits for a response to their action are interactive. Think of online shopping applications, which are offered by many retail businesses today. The interactive applications require human interaction and their response times are more important than for batch applications. However, strict response times or bandwidth guarantees might not be required, so if the appropriate amount of bandwidth is not available, then the transaction may take longer, but it will eventually complete. The main characteristics of the interactive applications are:
- Typically support human-to-machine interaction.
- Acceptable response times have different values depending on how important the application is for the business.
- Examples: database inquiry, stock-exchange transaction
- Real-time applications, such as voice and video applications, may also involve human interaction. Because of the amount of information that is transmitted, bandwidth is critical. In addition, because these applications are time critical, a delay on the network can cause a problem. Timely delivery of the data is crucial. It is also important that not too much data is lost during transmission because real-time applications, unlike other applications, do not retransmit lost data. Therefore, sufficient bandwidth is mandatory, and the quality of the transmission must be ensured by implementing QoS. QoS is a way of granting higher priority to certain types of data, such as Voice over IP (VoIP). The main characteristics of the real-time applications are:
- Typically support human-to-human interaction.
- End-to-end latency is critical.
- Examples: Voice applications, video conferencing, and live sports event online streaming.
Applications may also be required to manage different types of communications. One such application is the factory-automation application. Factory-automation applications deal with plant process-related data, such as readings from sensors and alarms, which require guaranteed delivery times and typically require feedback within a prescribed response time. On the other hand, the same factory-automation application must also handle certain device configurations and commercial data, which is not time-critical. cisco 200-301
Questions for cisco 200-301
Match the type of process to the correct application.
VoIP
interactive application
FTP
batch application
stock-exchange transaction
real-time application
Answer
The correct answers are: VoIP is a real-time application; An stock-exchange transaction is an interactive application; and FTP is considered a batch application.

CCNA 200-301 Portable Command Guide, 5th Edition. CCNA 200-301 Portable Command Guide is filled with valuable, easy-to-access information–and it’s portable enough to use whether you’re in the server room or the equipment closet. The guide summarizes all CCNA certification-level Cisco IOS Software commands, keywords, command arguments, and associated prompts, providing you with tips and examples of how to apply the commands to real-world scenarios. Throughout, configuration examples give you a better understanding of how these commands are used in simple network designs. Get Here
Question 2
Which network characteristic would best describe how well the network would support business critical applications in case of an unexpected increase of traffic?
- speed
- security
- QoS
- reliability
Question 3
You are given a physical network diagram. Which two statements about the logical diagram for the same network are true? (Choose two.)
- The logical diagram is obvious from the physical diagram.
- The logical diagram can be drawn by adding device model information to the physical diagram.
- The logical diagram can be drawn by examining device configurations.
- The logical diagram can be drawn by analyzing data flows in the network.
- The logical diagram is always different to the physical diagram.
Question 4
Which network characteristic indicates the dependability of the components that make up the network?
- reliability
- scalability
- security
- availability
Question 5
What is the function of a firewall?
- to automatically handle the configuration of wireless access points
- to allow wireless devices to connect to a wired network
- to connect networks and intelligently choose the best paths between networks
- to monitor and control the incoming and outgoing network traffic
Question 6
What are three examples of remote access locations? (Choose three.)
- branch offices
- head office
- small office/home office
- main office
- a network in an airport lounge
Question 7
What is the availability percentage over a one year period of the network that is not available for 15 minutes each month?
- 99.9657 percent
- 0.9996 percent
- 99.8457 percent
- 0.0342 percent
Question 8
What is the function of a WLAN controller?
- to monitor and control the incoming and outgoing network traffic
- to automatically handle the configuration of wireless access point
- to allow wireless devices to connect to a wired network
- to connect networks and intelligently choose the best paths between networks
Question 9
Which two statements about interface labels are true? (Choose two.)
- An interface label is part of the physical topology diagram.
- An interface label includes information about the interface type.
- An interface label is its IPv4 address.
- An interface label is used only when a device has more than one interface.
- An interface label can be arbitrarily selected by the device administrator.
Question 10
Which network characteristic indicates the general expense to purchase, install, and maintain network components?
- bandwidth
- security
- cost
- availability
CCNA 200-301 Complete Video Course and Practice Test. More Than 16 Hours of Video Instruction. CCNA 200-301 Complete Video Course is a comprehensive training course that brings Cisco CCNA exam topics to life through the use of real-world demonstrations, animations, live instruction, and configurations, making learning these foundational networking topics easy and fun. Get Here

Introducing the Host-To-Host Communications Model
Host-To-Host Communications Overview
ISO OSI Reference Model
TCP/IP Protocol Suite
Peer-To-Peer Communications
Encapsulation and De-Encapsulation
coming SOON……………………..

31 Days Before your CCNA Exam: A Day-By-Day Review Guide for the CCNA 200-301 Certification Exam. the friendliest, most practical way to understand the CCNA Routing & Switching certification process, commit to taking your CCNA 200-301 exam, and finish your preparation using a variety of primary and supplemental study resources. Get Here
Cisco CCNA 200-301 Exam: Complete Course with practical labs
The complete course to help you prepare and pass Cisco’s newest CCNA 200-301 exam. Everything you need: Theory and labs
What you’ll learn
- This course is for anyone who wants to attain the Cisco CCNA 200-301 certification
- Once you complete this course and pass your CCNA exam, you can study towards higher-level Cisco certifications
- This course will prepare you for the CCNA 200-301 certification exam.
- Learn how Kali Linux can be used to hack networks
- Learn how to configure Cisco Routers and Switches
- Learn topics such as Wi-Fi, Network Automation and Network Security
- This course is practical! Once you complete the course, you will be able to apply what you have learned to real-world networking scenarios.
This course is unlike other CCNA courses as it contains:
* Large amount of practical video content with detailed explanations of CCNA topics and GNS3 and Cisco Packet Tracer demonstrations
* Built in Packet Tracer assessments and labs. Massive amount of practical, hands-on content that you can use to study offline.
* Software – Subnetting Calculators, Config-Register, binary & hexadecimal & decimal calculators
* Many demonstrations showing you practically how to configure and build Cisco networks
* Cheatsheets
* Quiz questions
