CCNA Practice tests. CCNA exam is now 200-301. Here are free practice tests questions and answers. try this 25 questions with answers. for CCNA exam practice. OSI/TCP Model Questions Q1.…
Cisco CCNA practice test: Try these 20 exam questions

Cisco CCNA practice test
Use this CCNA latest practice test as study material to prepare for the Cisco CCNA Routing and Switching exam. With 20 questions..
Achieving your Cisco Certified Networking Associate, or CCNA, certification requires more than just studying. Instead, it takes a true in-depth understanding of network fundamentals and network security technologies covered in the CCNA material as outlined by Cisco. Our updated CCNA practice test has been redesigned to reflect the Cisco CCNA Routing and Switching requirements.

In 2019, Cisco announced a new CCNA Routing and Switching exam. Beginning Feb. 24, 2020, the new 200-301 exam will replace the existing 200-125 exam. If you’ve been studying for your CCNA using the version 3.0 study materials, it is highly advisable you take the older 200-125 exam while you still can.
This CCNA practice test covers the appropriate range of topics you can expect when taking the CCNA Routing and Switching exam. The practice questions are in no particular order and provide a realistic example of what you should expect.
QUIZ for Cisco CCNA practice test

QUESTION 1
Which Rapid Spanning Tree Protocol port state is a combination of standard 802.1D STP’s disabled, blocking and listening states?
- Blocking
- Discarding
- Learning
- Forwarding
- Listening
CORRECT ANSWER – Discarding
MORE INFORMATION:
Rapid Spanning Tree Protocol (RSTP) defines three port states, compared with 802.1D STP’s five states. RSTP combines the disabled, blocking and listening states into a single port state known as discarding.
The reason for the combination is because a port in a disabled, blocking or listening state doesn’t differ from an STP topology perspective. Each of these states discards all frames and isn’t actively learning the media access control (MAC) addresses of connected switches and devices.
QUESTION 2
Host A receives a frame and discards it after determining it is corrupt. Which OSI layer checks frames for errors?
- Application
- Network
- Physical
- Data-link
- FCS or CRC
CORRECT ANSWER – Data-link
MORE INFORMATION:
The data-link layer is responsible for checking each received frame for errors. Every Ethernet frame includes the frame check sequence (FCS) or cyclic redundancy check value that is calculated by the host that sent the frame.
The receiving host generates its own FCS value for every frame received and then compares it with the FCS included in the frame. If the FCS values match, the frame has arrived without any error. If the FCS values don’t match, then the host assumes the frame has an error or is corrupt and, therefore, discards it. More information on Ethernet frames can be found on Firewall.cx’s Ethernet frame analysis page.
Cisco CCNA practice test
QUESTION 3
No matter how it’s configured, a single switch port is considered what?
- A separate unicast domain
- A separate broadcast domain
- A separate multicast domain
- A separate collision domain
CORRECT ANSWER – A separate collision domain
MORE INFORMATION:
Unlike a network hub, which is a single collision domain for all ports, each port on a Layer 2 switch is a separate collision domain.
QUESTION 4
Identify which of the services below uses both TCP and UDP ports.
- FTP
- TFTP
- DNS
- SSH
- Telnet
CORRECT ANSWER – DNS
MORE INFORMATION:
The DNS protocol is the only protocol of those listed above that uses both the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). UDP is the preferred transport protocol for DNS services because it is fast. UDP doesn’t require a connection to be established between the hosts before sending any data.
If a host fails to receive a response from a DNS server after several requests, it can then switch to TCP. TCP is slower, but more reliable, because it requires a three-way handshake to be established between the hosts before any data is sent.
Cisco CCNA practice test

QUESTION 5
A router with a BGP autonomous system number of 65001 is peered with another router with the same BGP AS. Which of the following is true?
- The ebgp multihop command must be configured to reach an established state.
- A BGP connection will be established, but no traffic will traverse the connection.
- The routers are considered eBGP neighbors.
- The routers are considered iBGP neighbors.
- A BGP establishment error will occur because of the AS conflict.
CORRECT ANSWER – The routers are considered iBGP neighbors.
MORE INFORMATION:
When two routers belong to the same autonomous system bearing the same AS number, they are considered internal BGP, or iBGP, neighbors. This also means the routes learned between these neighbors use the internal BGP administrative distance of 200, as opposed to the external AD of 20.
QUESTION 6
What is the default 802.1D short spanning tree port cost of a 10 Gbps Ethernet link?
- 10
- 4
- 2
- 2,000
CORRECT ANSWER – 2
MORE INFORMATION:
By default, the 802.1D path cost for a 10 Gbps link is 2 using the short 16-bit method. If you calculate the same link using the long 32-bit method, you get a default value of 2,000.
QUESTION 7
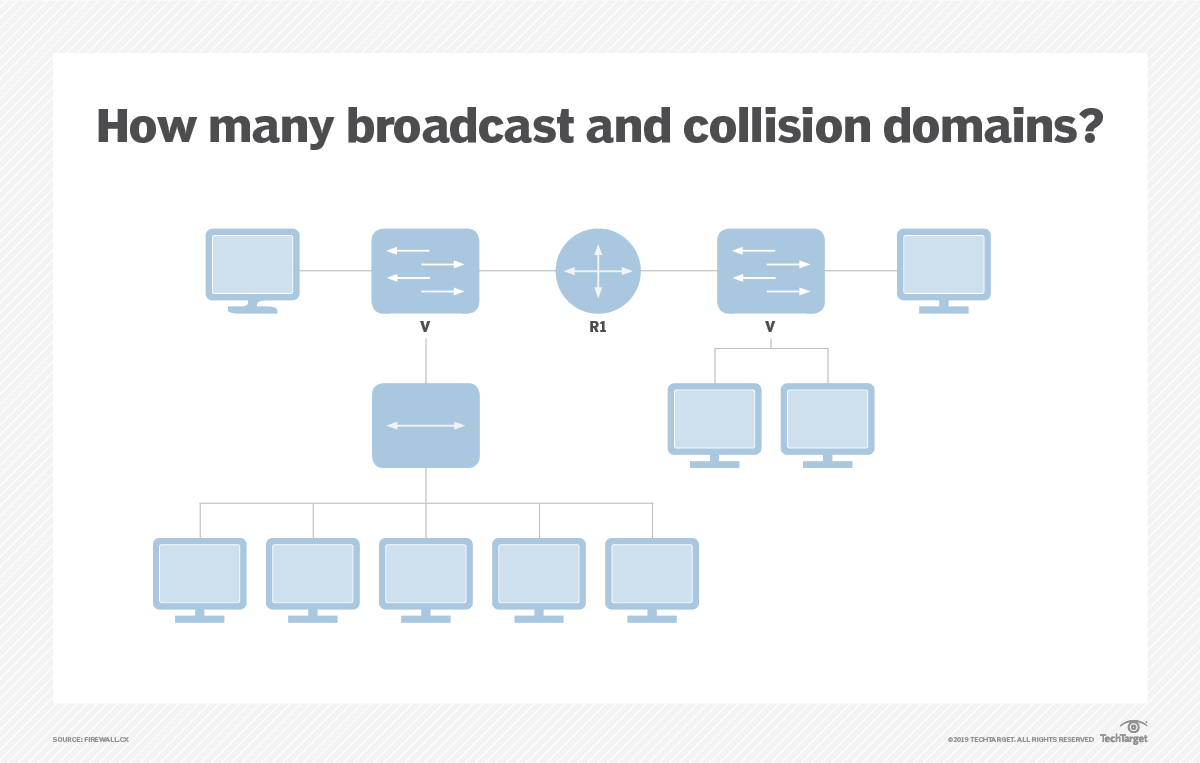
After carefully examining the network diagram above, select the correct statement regarding broadcast and collision domains.
- There is one broadcast domain and seven collision domains.
- There are two broadcast domains and five collision domains.
- There is one broadcast domain and 12 collision domains.
- There are two broadcast domains and seven collision domains.
- There are two broadcast domains and 12 collision domains.
CORRECT ANSWER – There are two broadcast domains and seven collision domains.
MORE INFORMATION:
Each link to a switch — switch port — is a separate collision domain. In our diagram, we have two switches and a total of seven links. Hubs — located in the lower left corner of the image — do not create separate collision domains per link. That’s because traffic entering one port exits all other ports.
Routers, on the other hand, create separate broadcast domains, as broadcast packets do not propagate across them.
Cisco CCNA practice test
QUESTION 8 Cisco CCNA practice test
Which of the following is the correct syntax to configure a switch port as a standard user port on VLAN 10 for data and VLAN 50 for VoIP?
- TechTarget-SW1(config-if)#switchport mode trunk
TechTarget-SW1(config-if)#switchport access vlan 10
TechTarget-SW1(config-if)#switchport voice vlan 50 - TechTarget-SW1(config-if)#switchport mode access
TechTarget-SW1(config-if)#switchport access vlan 10
TechTarget-SW1(config-if)#switchport voice vlan 50 - TechTarget-SW1(config-if)#switchport mode trunk
TechTarget-SW1(config-if)#switchport access vlan 10
TechTarget-SW1(config-if)#switchport voip vlan 50 - TechTarget-SW1(config-if)#switchport mode access
TechTarget-SW1(config-if)#switchport access vlan 10
TechTarget-SW1(config-if)#switchport voip vlan 50 - TechTarget-SW1(config-if)#switchport mode access
TechTarget-SW1(config-if)#switchport access vlan 50
TechTarget-SW1(config-if)#switchport voice vlan 10
CORRECT ANSWER – TechTarget-SW1(config-if)#switchport mode access
TechTarget-SW1(config-if)#switchport access vlan 10
TechTarget-SW1(config-if)#switchport voice vlan 50
MORE INFORMATION:
When configuring a user port for both voice and data, follow three steps. The first step is to define the port as an access port, as opposed to a trunk port. Second, configure the access virtual LAN to the VLAN ID of standard data traffic. Finally, you must configure the voice VLAN to the appropriate VLAN ID.
Cisco CCNA practice test
QUESTION 9

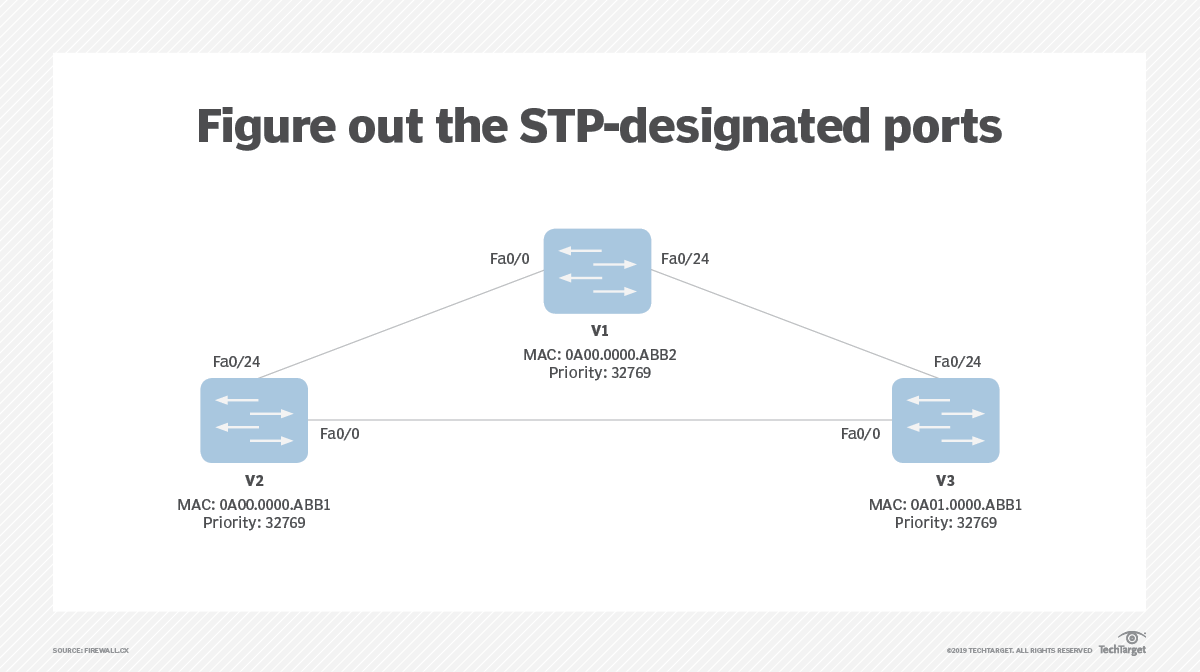
Your manager has requested you indicate which of the above ports will be Spanning Tree Protocol-designated ports.
- Switch V1, Port Fa0/0; Switch V3, Port Fa0/0; Switch V3, Port Fa0/24
- Switch V1, Port Fa0/24; Switch V2, Port Fa0/0; Switch V2, Port Fa0/24
CORRECT ANSWER – Switch V1, Port Fa0/24; Switch V2, Port Fa0/0; Switch V2, Port Fa0/24
MORE INFORMATION:
The first step is to understand which switch will become the root switch. This is done via a process called the STP root bridge election process. According to this process, the switch with the lowest bridge ID will be elected as the root switch. In our network diagram, that’s SwitchV2.
As per STP protocol, SwitchV2 will have all ports set to STP designated. Ports Fa0/0 on SwitchV1 and SwitchV3 are used to reach the root switch and are, therefore, designated STP root ports.
The last set of ports to examine is Fa0/24 on SwitchV1 and SwitchV3. Between these two, one port must be set to blocking mode in order to avoid creating a loop in our network, while the other will be set to forwarding mode. SwitchV1 wins because it has a lower MAC address, so SwitchV1 Fa0/24 is set to forwarding and becomes an STP-designated port, while SwitchV3 Fa0/24 turns to a blocking state.
Detailed examples and analysis on STP, bridge election and STP port states can be found on Firewall.cx’s STP section.

QUESTION 10
Which of the following EXEC commands will reset LLDP traffic error counters?
- clear lldp
- clear lldp all
- clear table lldp
- clear lldp table
- clear lldp counters
CORRECT ANSWER – clear lldp counters
MORE INFORMATION:
The correct syntax to reset Link Layer Discovery Protocol (LLDP) traffic and error counters to zero is clear lldp counters. The clear lldp table command will delete the LLDP table of any information about learned neighbors. All other answers have incorrect or incomplete syntax.
QUESTION 11
One of the routers in your company has just received information about network 172.16.10.0/24 from multiple sources. Which of the below will the router consider as the most reliable source for network 172.16.10.0/24?
- An EIGRP update for network 172.16.10.0/24
- An OSPF update for network 172.16.10.0/24
- A static route to network 172.16.10.0/24
- A default route with a next hop address of 172.16.0.1
- A directly connected interface with an IP address of 172.16.10.254/24
- None of the above. The router will discard the update.
YOUR ANSWER – A directly connected interface with an IP address of 172.16.10.254/24
MORE INFORMATION:
The administrative distance is used by a router to determine which routing protocol to use if two or more protocols provide routing information for the same destination network. The smaller the administrative distance is, the higher the preference.

Directly connected interfaces have an AD of 0 and are always preferred. Static routes have an AD of 1, while the Enhanced Interior Gateway Routing Protocol (EIGRP) has an AD of 90, and Open Shortest Path First (OSPF) has an AD of 110.
QUESTION 12
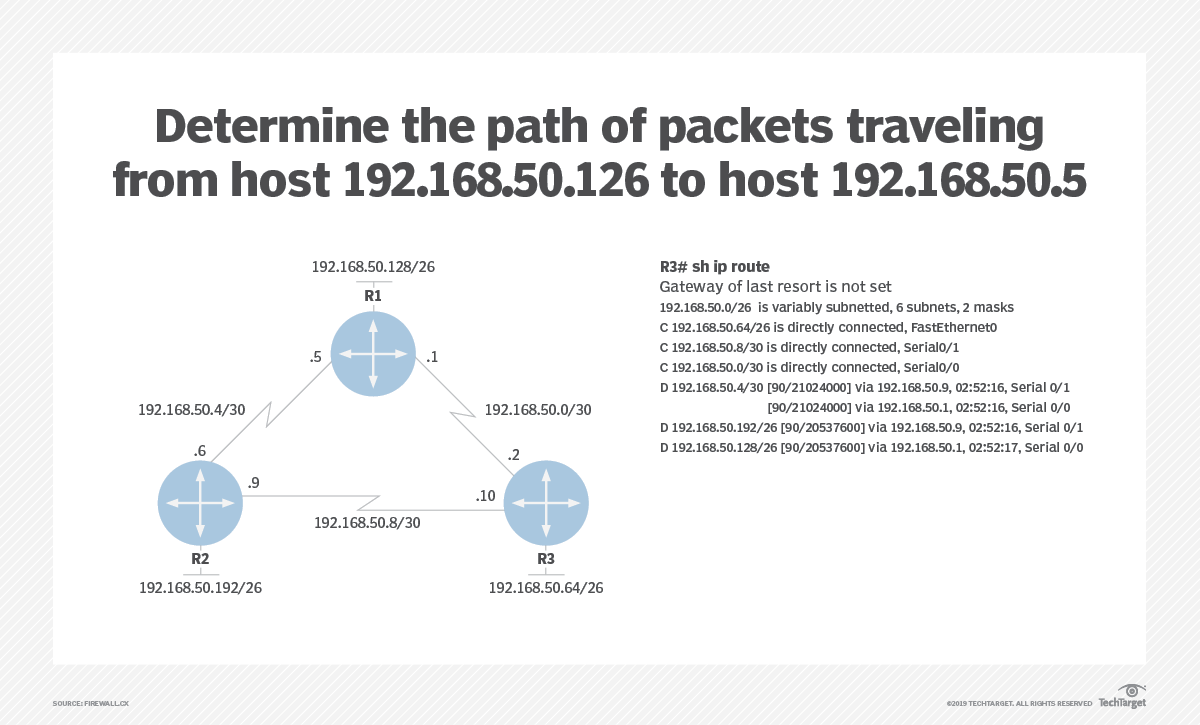
In the network diagram above, which path will packets take when traveling from host 192.168.50.126 to host 192.168.50.5?
- Packets will travel from R3 to R2 to R1.
- Packets will travel from R1 to R3 to R2.
- Packets will travel from R3 to R1 and return back to R3.
- Packets will travel from R3 to R1 and from R3 to R2 to R1.
- Packets will travel from R1 to R2 and back.
CORRECT ANSWER – Packets will travel from R3 to R1 and from R3 to R2 to R1.
MORE INFORMATION:
We begin by identifying to which network host 192.168.50.126 belongs. IP address 192.168.50.126 is the last usable address for network 192.168.50.64/26, which means it is directly connected to Router 3.
Next, we need to identify where 192.168.50.5 is located. By examining the diagram, we can see IP 192.168.50.5 is Router 1’s interface that connects directly with Router 2.
Finally, to understand the path packets will take, we examine the output of Router 3’s routing table and discover there are two equal cost links to network 192.168.50.4/30. So, EIGRP will load-balance between both paths.
QUESTION 13
Which of the following options are used in standard access lists?
- Destination address and subnet mask
- Source address and subnet mask
- Destination address and wildcard mask
- Source address and wildcard mask
CORRECT ANSWER – Source address and wildcard mask
MORE INFORMATION:
Standard access lists provide a simple set of options: the source address and wildcard mask. Extended access lists offer additional options — source address, destination address, wildcard mask, protocol and ports — thus providing greater granularity.
In both cases, it’s important to remember access lists always use the wildcard mask, which is the reverse of a subnet mask.
QUESTION 14
When configuring NAT, what is the purpose of the overload command, as used in the following example:Router(config)#ip nat inside source list 1 interface gi0/2 overload
- It translates a single local address into many global addresses by tracking the connection’s UDP port number.
- It indicates a one-to-one translation on the interface by tracking the connection’s TCP port number.
- It translates many local addresses into a single global address by tracking the connection’s TCP port number.
- It translates a single local address into many global addresses by tracking the connection’s TCP port number.
- It translates many local addresses into a single global address by tracking the connection’s UDP port number.
CORRECT ANSWER – It translates many local addresses into a single global address by tracking the connection’s TCP port number.
MORE INFORMATION:
The example configuration will use the single IP address assigned to interface gi0/2. Any internal — local — IP that attempts to communicate with a device on the other side of gi0/2 will be translated to this single address.
The router will maintain a NAT table for this connection. This table contains the local IP address of the internal device, the single IP to which it is translated and a unique TCP port number that is used to identify packets within that particular conversation.
QUESTION 15
Which statement about NTP is true?
- A stratum 2 NTP server is directly attached to an authoritative time source.
- NTP must be configured to synchronize with one of a handful of atomic clocks available on the internet.
- NTP authentication is disabled by default.
- You must configure two or more NTP sources for times to be accurate.
CORRECT ANSWER – NTP authentication is disabled by default.
MORE INFORMATION:
By default, NTP authentication is disabled. To configure it, you must set the authentication-key, trusted-key number and then enable the features using the NTP authenticate command.
QUESTION 16
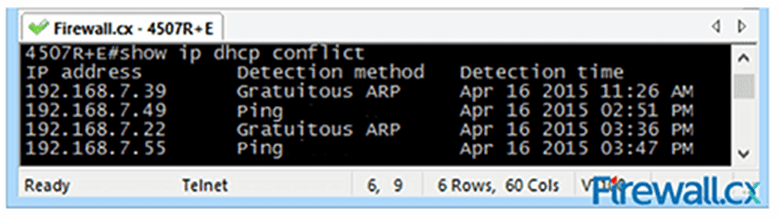
What actions does the DHCP server take when there is an IP address conflict, as shown above?
- The DHCP server will automatically resolve all conflicts after their lease is over.
- The IP addresses are removed from the DHCP pool until the conflicts are resolved.
- The IP addresses detected by gratuitous Address Resolution Protocol are removed from the pool.
- The IP addresses detected by ping are removed from the pool.
- The DHCP server needs to be restarted in order to automatically clear all conflicts.
CORRECT ANSWER – The IP addresses are removed from the DHCP pool until the conflicts are resolved.
MORE INFORMATION:
When a Cisco DHCP server discovers a conflict, it will place the IP address into the conflict table, stating the address was conflicting and how it came to that conclusion, as noted under the detection method column.
The administrator must examine each IP address and detection method and, when ready, clear the IP addresses from the conflict pool. More information on each detection method and commands to clear them can be found on Firewall.cx’s DHCP article.
QUESTION 17
What would the result be when the following commands are executed on a Cisco Catalyst switch:TechTarget-SW1 (config-if)# switchport port-securityTechTarget-SW1 (config-if)# switchport port-security mac-address sticky
- The MAC address learned dynamically is saved in the switch’s running-configuration.
- The MAC address learned dynamically is saved in the switch’s startup configuration.
- The MAC address learned dynamically is saved permanently in the VLAN database.
- The statically configured MAC address is saved in the switch’s running configuration when frames from that address are received.
- The first MAC address seen on the specific port is allowed to access the network until the port security timer expires.
CORRECT ANSWER – The MAC address learned dynamically is saved in the switch’s running-configuration.
MORE INFORMATION:
When the switch port-security mac-address sticky command is used without specifying a MAC address at the end, the MAC address of the attached device is dynamically learned and placed in the running configuration of the switch.

QUESTION 18
Which of the following is not an IPv6 address type?
- Broadcast
- Unicast
- Anycast
- Multicast
CORRECT ANSWER – Broadcast
MORE INFORMATION:
Unlike IPv4, the IP version 6 (IPv6) protocol does not use a broadcast address type. For bandwidth efficiency purposes, the duties of IPv4’s broadcast addressing have been incorporated into IPv6 multicast addressing.
QUESTION 19
A router has two identical default routes to 10.0.0.0/24. One route is learned via EIGRP, and the other is a static route. Which of the following commands will set the static route so it’s only used in the event the EIGRP route is no longer available?
- ip route 10.0.0.0 255.0.0.0 192.168.1.254 10
- ip route 10.0.0.0 255.0.0.0 192.168.1.254 100
- ip route 10.0.0.0 255.0.0.0 192.168.1.254 distance 10
- ip route 10.0.0.0 255.0.0.0 192.168.1.254 distance 100
CORRECT ANSWER – ip route 10.0.0.0 255.0.0.0 192.168.1.254 100
MORE INFORMATION:
Adjusting the administrative distance so it is higher than a dynamically learned AD is known as a floating static route. Floating static routes are often used as a failover mechanism in the event the dynamically learned path fails. The proper syntax to change the AD is to simply type it at the end of the next-hop route. The distance can be set to anything between 1 and 255. In this example, the AD must be set higher than 90, as this is the default AD used by internal EIGRP.

QUESTION 20
Which Ethernet switching method would you use if low latency is of utmost importance?
- First-in-first-out
- Store-and-forward
- Cut-through
- Cisco Express Forwarding (CEF)
- Queuing
CORRECT ANSWER – Cut-through
MORE INFORMATION:
Cut-through provides the lowest-latency switching available. It forwards Ethernet packets faster than any other method, because it only waits to read the destination MAC address before forwarding.














